Become CEH (certified ethical hacker) v11 | Study Guide | Groundcyber
CEH (certified ethical hacker) course overview:
The EC-Council-accredited CEH (Certified Ethical Hacker) course is designed to help you understand the key ethical hacking skills and techniques, including penetration testing, enumeration, sniffing, vulnerability analysis, SQL injection, network packet analysis, etc. It is matched with the CEH v11 exam.
Here are some examples of what makes CEH v11 unique from other versions:
Mapped to NICE 2.0
You will have access to the NICE 2.0 framework in this course, which clearly explains all the facts surrounding the new standards and procedures. As a federal employee, Protect and Defend (PR), Analyze assist you advance in your career.
Practical Hacking Tasks
You will receive new hacking tasks, tricks, and information on upcoming changes in the cyber realm. You develop and showcase your abilities and use your razor-sharp edges.
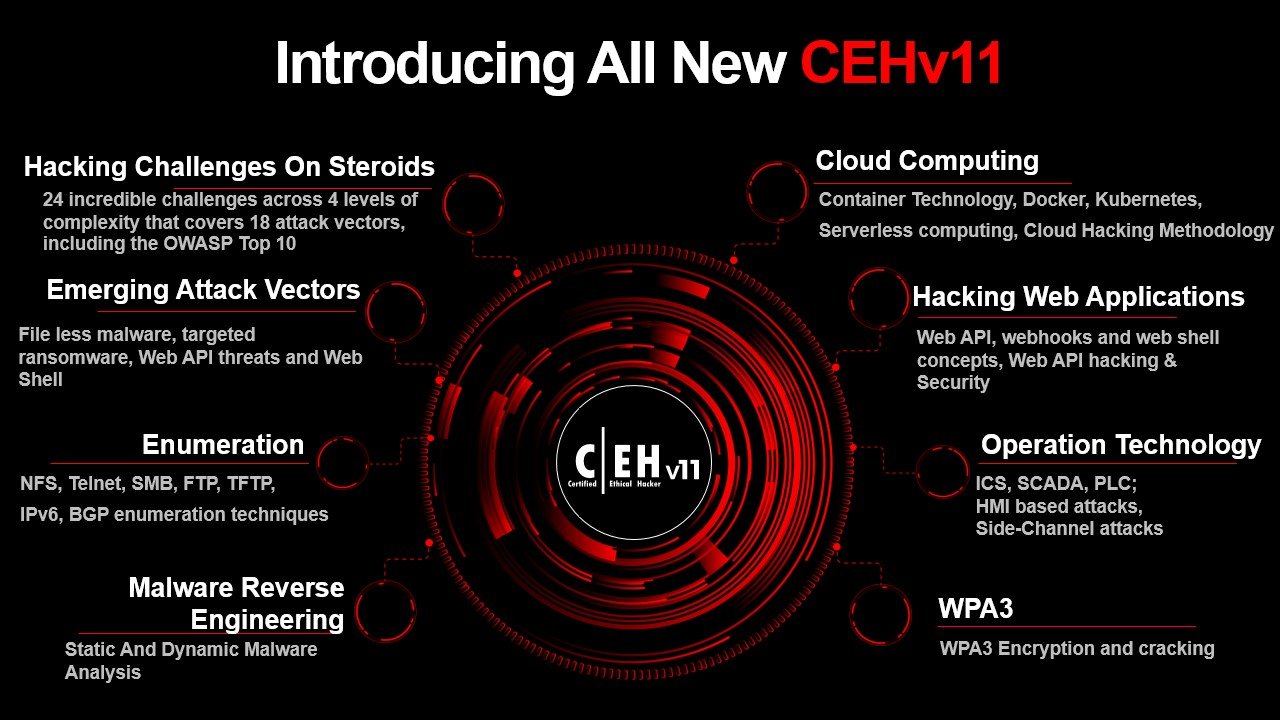
Emerging Attack Vectors
The increased attention to 18 attack vectors, including the OWASP Top 10, IoT hacking, vulnerability analysis, APT, malware, web API threats, webhooks, web shells, OT attacks, cloud attacks, AI, ML, and much more!
Modern case studies and current events
Learn about current events and how things have changed over time in the new ethical hacking version. To work on such issues more effectively and evaluate them for better outcomes.
unique hacking tools, methods, and tactics.
The CEH v11 builds on its history by introducing you to the newest hacking methods, including fileless malware, sophisticated social engineering tactics, and more. Get familiar with the most cutting-edge hacking tools.
Increased Attention to Malware Analysis
In CEHv11, you will gain a thorough understanding of malware as well as steps you can take to protect IoT, Android, and financial systems against ransomware.
Why is there a need for ( CEH) certified ethical hackers?
- In 2021, there will likely be 3.5 million unfilled cybersecurity positions.
- Nowadays, almost every business has a cybersecurity role to safeguard its data, applications, infrastructure, devices, and employees.
- By 2021, 99% of significant businesses will offer CISO positions for hire.
- According to a technical study done by MIT, only one out of every four security experts is competent to work in cybersecurity.
The Key Features of CEH (certified ethical hacker) Training
An accredited training partner of the EC-Council.
The official training partner of the EC Council is Ground Cyber. Obtain Certified Hacker status. Ground Cyber offers Ec Council training and certification.
Live Video Session
5X more interaction during live online classes led by subject-matter experts to make it simple for students to comprehend the material.
technical support.
We are available 24/7/365 to respond to your inquiries. Contact us for general assistance, queries, requests for collaboration, or anything else relating to our services.
Course Outline of CEH (certified ethical hacker) Certification
Eligibility
This ethical hacking course is intended for network security officers, site administrators, IS/IT analysts, IS/IT auditors, IT operations managers, IT security officers, network specialists, and other employees in related computer support and information technology departments.
Pre-requisites
The prerequisite for learners is either a high school diploma or an undergraduate degree. You can do it after the 10th & 12th.
The CEH (certified ethical hacker) certification course outline covers an array of topics in today’s digital world, from malware analysis to penetration testing.

Module 1: Introduction to Ethical Hacking
It includes all the basics of ethical hacking.
Module 2:Footprinting and Reconnaissance
This subject teaches you how to do footprinting and reconnaissance using the most recent methods and equipment.
Module 3: Scanning Networks
In this module, you learn different network scanning techniques.
Module 4: Enumeration
You learn many enumeration strategies in this topic, including network file sharing (NFS), related countermeasures, etc.
Module 5: Vulnerability Analysis
This subject teaches you how to spot security gaps in the network and core systems of a targeted company.
Module 6: System Hacking
In this module, you learn about system hacking methods—including steganography, covering tracks, etc.
Module 7: Malware Threats
Malware dangers In this module, you learn about the various varieties of malware, including viruses, Trojan horses, and worms, as well as malware analysis and countermeasures.
Module 8: Sniffing
This lesson teaches you how to find network vulnerabilities by using packet-sniffing techniques.
Module 9: Social Engineering
This module is dedicated to social engineering concepts and techniques, including identifying theft attempts and suggesting social engineering countermeasures.
Module 10: Denial of Services
In this module, you learn different denial services and attack techniques, in addition to the tools used to audit a target and its protections.
Module 11: Session Hijacking
In this module, you will understand various sessions of hijacking techniques used to discover network-level session management, authorization, cryptographic weaknesses, etc.
Module 12: Evading IDS, Firewalls, and Honeypots
In this module, you’ll be introduced to a firewall, an intrusion detection system, and honeypot evasion techniques; the tools used to audit a network perimeter for weaknesses.
Module 13: Hacking Web Servers
In this module, you learn about web server attacks, including comprehensive attack methodology used to audit vulnerabilities in web server infrastructure and countermeasures.
Module 14: Hacking Web Applications
In this module, you learn about web application attacks, including a comprehensive web application hacking methodology used to audit vulnerabilities in web applications and countermeasures.
Module 15: SQL Injection
In this module, you learn SQL injection attack techniques, injection detection tools, and countermeasures to detect and defend against SQL injection attempts.
Module 16: Hacking Wireless Networks
In this module, you learn about wireless encryption, wireless hacking methodologies and tools, and Wi-Fi security tools.
Module 17: Hacking Mobile Platforms
In this module, you learn about mobile platform attack vectors, Android vulnerabilities exploited, and mobile security guidelines and tools.
Module 18: IoT Hacking
In this module, you learn how to secure and define the Internet of Things and operational technology devices and possible threats to IoT and OT platforms.
Module 19: Cloud Computing
In this module, you learn about various cloud computing concepts, such as container technologies and serverless computing; various cloud-based threats and attacks; and cloud security techniques and tools.
Module 20: Cryptography.
This is the final module. In this module, you learn about cryptography and ciphers, public-key infrastructure, cryptography attacks, and cryptanalysis tools.
- Total Number of Questions: 125
- Test Time Duration: 4 hours
- Test Format: Multiple Choice
- Test Delivery: ECC EXAM, VUE
- Exam Prefix: 312-50(ECC EXAM), 312-50(VUE)
- Passing Score in CEH Certification: Depending on which exam form is challenged, cut scores can range from 60% to 85%.
- There are many job roles for CEH professionals, but some of the most common include:
- penetration tester
- Security Consultant
- An information security analyst
- Systems Administrator
- Manual of Ethical Hacker
- A network security engineer
- Junior Penetration Tester
CEH EXAMS
Use online, hands-on exams to demonstrate your knowledge and abilities.

EC-Council also provides training and vouchers.
Visit the Ground Cyber website for all the details. We offer the best IT training services in the region. To address client needs, we have fresh, creative ideas. We are a reputable and expanding IT security expert. We are providing The LPT (Master) certification voucher for every student.



